How Organizations Defend Against the Unknown Dark Web Threats?
The internet plays a crucial role in our digital era, providing unparalleled connectivity and convenience in our daily routines. Yet, beneath its surface, lies a concealed realm known as the Dark Web. This hidden landscape becomes a breeding ground for illicit operations, giving rise to cyber threats that wield substantial influence over worldwide enterprises. This blog delves into the uncharted territory of the internet – the enigmatic Dark Web – and unveils the potential hazards it poses to businesses.
What Exactly Is the Dark Web?
To truly grasp the concept of the dark web, we first need to delve into the idea of the deep web. The deep web encompasses parts of the internet that search engines like Google can’t access. It’s important to note that many sites within the deep web are perfectly legal – they simply don’t utilize traditional links that appear in search engine results.
For instance, government databases and personal information like banking details of everyday internet users are securely housed in the deep web. Interestingly, about 96% of online content resides here, primarily comprising sensitive data safeguarded under layers of security. Search engines don’t index this information to maintain its confidentiality.
A much smaller portion of the deep web constitutes the dark web, and gaining access often requires anonymizing encryption tools like TOR. This corner of the internet has earned notoriety for hosting illegal activities, including drug trade, prohibited pornography, and weapons sales.
Understanding this layered landscape of the internet, from the expansive deep web to the cryptic dark web, is pivotal in comprehending the intricate digital environment that influences our online experiences and, at times, presents significant cybersecurity challenges.
How Do Dark Web Hackers Target Businesses?
Hold onto your digital hats as we plunge into the intriguing world of the Dark Web, where crafty cyber crooks have their eyes set on businesses like yours.
Imagine a secret digital black market – the Dark Web – where stolen company secrets are the currency of choice. It’s like a hackers’ shopping spree, with your confidential intel up for grabs. From employee records to financial skeletons, everything’s in the mix. Why? Because payday awaits – they can auction off your info or use it to wreak ransomware havoc.
But how does your data end up in this cyber underworld? Meet the ‘hacktivists’ – the digital daredevils seeking online street cred. They break into your virtual fortress, flaunting your swiped data online for the thrill or, worse, to tarnish your business rep.
And there’s a twist! Even your trusted employees can unknowingly drop the ball. One misstep with a phishing email, and poof, there goes the data! Keep an eye out for the ‘script kiddies’ too – these cyber scouts cruise the virtual alleys, seeking unprotected digital doors. They scan websites and servers, looking for their next jackpot.
What Role Does the Dark Web Play in Data Breaches?
Ever wondered where stolen data goes? Welcome to the Dark Web, hackers’ secret lair where stolen information finds its buyers, law enforcement is dodged, and the data breach game thrives.
Imagine this: a data breach occurs. But the story doesn’t end there. Hackers dive into the Dark Web’s underground markets and forums, putting up their loot for sale. And how do they do it? Through Tor, the secret gateway. It’s like the secret entrance to a digital speakeasy. Tor’s encrypted paths ensure that buyers and sellers remain in the shadows, making transactions smooth and secure. Cyber crooks revel under cover, adopting fake identities and avoiding the spotlight.
Now, how can organizations fight back? It’s not just about cyber armor – though that’s essential. Regular security checkups, employee cyber drills, and advanced threat-spotting tech are all weapons in this battle. But it doesn’t stop there. Think teamwork. Law enforcement, cyber experts, and private defenders unite to tackle these digital villains. It’s a cyber showdown, where collaborative resilience stands guard over your data.
How Cybercriminals Profit from Data on the Dark Web?
Ever wondered how the hidden corners of the internet function? Let’s embark on a journey into the captivating realm of the Dark Web’s data trade, where stolen information holds value and anonymity reigns supreme.
Envision hackers as contemporary digital traders, setting up virtual stalls in enigmatic forums. Their virtual shelves display a myriad of pilfered treasures – online data, passwords, and even coveted organization PII. Why these forums, you might ask? Anonymity becomes their cloak, security their fortress, and the ever-elusive nature of shutting down these digital hideouts fuels their persistent return.
Now, brace yourself for the twist. Unlike the commonplace surface web, where a few keystrokes unlock a world of information, the Dark Web shrouds itself in secrecy. It’s a members-only club, accessible via clandestine links or exclusive invitations. Picture a digital speakeasy, sans the neon sign. This exclusivity safeguards data transactions, shrouding them from prying eyes.
Introducing the protagonists of our narrative: the security professionals. Modern-day detectives, equipped with specialized skills, navigate the intricate web of intrigue, unveiling the truth behind data breaches. Armed with expertise, they navigate this digital labyrinth, illuminating the darkest corners of the cyber underworld.
How do Vulnerability Assessment and Penetration Testing (VAPT) Services Protect you from Dark Web Threats?
In the ever-evolving landscape of cybersecurity threats, Vulnerability Assessment and Penetration Testing (VAPT) services stand as formidable defenders against the shadows cast by the dark web. By seamlessly integrating VAPT services into their cybersecurity strategy, organizations equip themselves to effectively combat these threats. Let’s explore how:
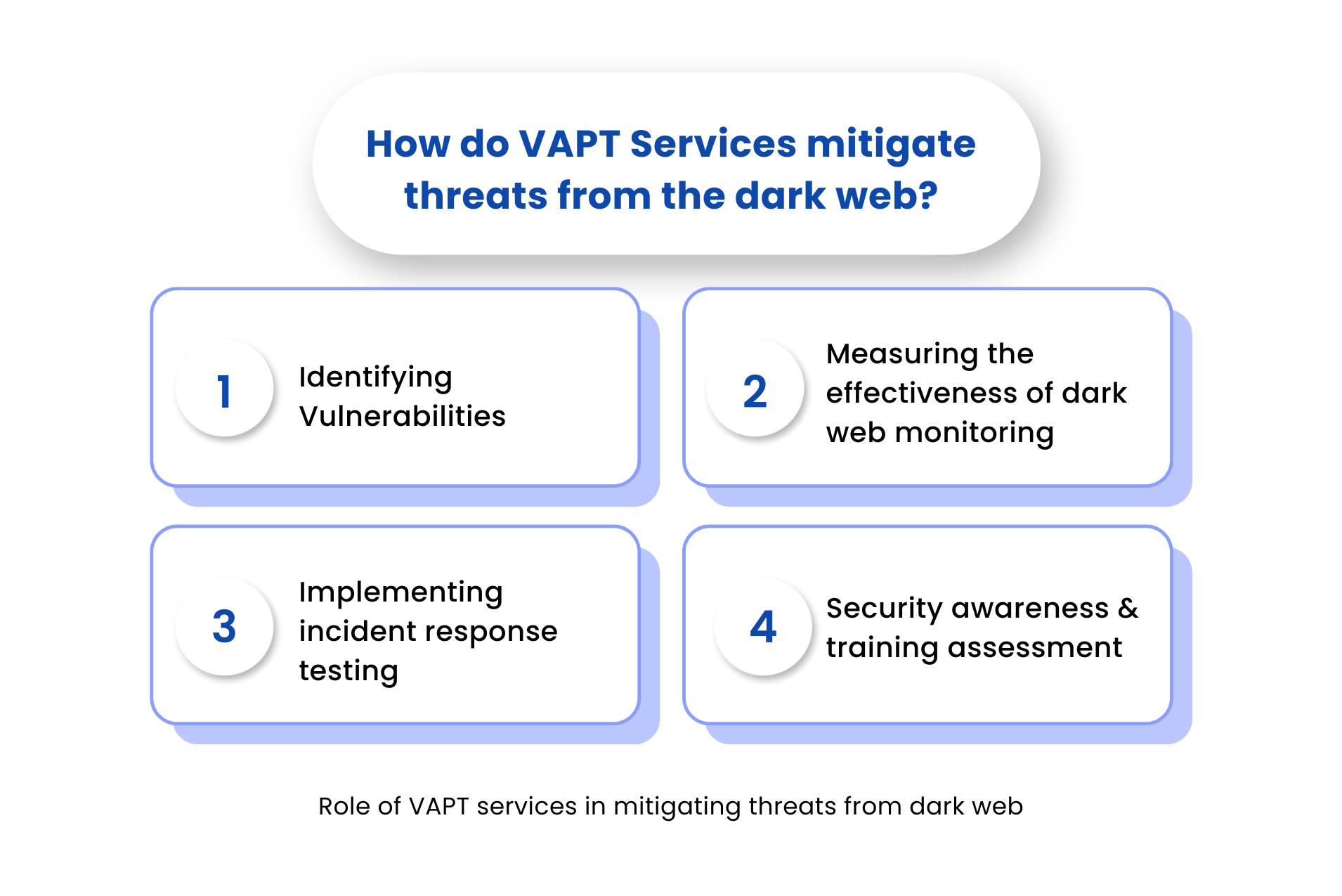

Spotting Vulnerabilities
VAPT services enlist the expertise of cybersecurity professionals who meticulously scan an organization’s digital infrastructure to unveil vulnerabilities commonly exploited by hackers. This proactive approach empowers organizations to seal security gaps before unauthorized access can compromise sensitive data, thwarting potential data breaches.
Assessing Dark Web Monitoring
Enterprises adopting VAPT can evaluate the effectiveness of their monitoring efforts. Through simulated attacks that mimic potential threats originating from the dark web, penetration testers assess an organization’s security systems’ responsiveness. This evaluation guides organizations in refining their monitoring capabilities, enhancing threat detection, and elevating response mechanisms.
Testing Incident Response
At the heart of VAPT services lies penetration testing, a pivotal practice that replicates cyber assaults, including those potentially arising from the dark web. This exercise empowers organizations to measure the efficacy of their incident response and business continuity strategies when facing potential threats. By pinpointing gaps and vulnerabilities, organizations enhance their readiness to mitigate real-world cyber attacks.
Evaluating Security Awareness and Training
VAPT services transcend mere technological evaluations. They extend their reach to assess an organization’s workforce security awareness and training. This aspect proves especially crucial in combating insider threats, where employees may be tempted into collaboration with cybercriminals. VAPT services contribute to fostering a robust security culture, mitigating insider risks, and enhancing overall cybersecurity practices.
Effective Strategies to Defend Against Cyber Threats from the Dark Web
Guarding your company’s digital fortress against the lurking perils of the Dark Web doesn’t have to be a labyrinthine challenge. There’s a spectrum of strategies at your disposal, ranging from simple steps for your team to wield, to cutting-edge tools that bolster your data’s security.
- Strengthen with Smart Passwords: Forge passwords that fuse upper and lower case letters, numerals, and symbols. The more unique your password, the more formidable the defense.
- Rotate Passwords Regularly: Keep cyber invaders on their toes by routinely changing passwords. Consider crafting imaginative, but misleading, responses to security questions.
- Embrace Password Diversity: Safeguard each account with a distinct password. Employ a reliable password manager like LastPass to keep these keys in order.
- Shield with Security Software: Install a firewall, anti-spyware, and antivirus software to create an impenetrable barrier against malware and phishing attempts.
- Establish Clear Internet Guidelines: Educate your staff on safe Internet practices. Teach them to steer clear of unsolicited links and consider curbing the use of personal devices on your company’s network.
- Elevate Security with a VPN: Enlist a Virtual Private Network (VPN) to cloak your online activities from prying eyes. This digital cloak conceals your location and history, frustrating unauthorized access.
- Bolster with Two-Factor Authentication: Fortify online accounts with two-factor authentication (2FA), rendering hackers’ efforts futile.
- Verify Website Security: Before making online transactions, ensure the website’s URL starts with ‘https’ and features the padlock icon, signifying a secure connection.
- Partner with Expert IT Services: Safeguard your business by tapping into the expertise of seasoned IT professionals. At Onestop IT, we specialize in crafting tailored cybersecurity solutions to shield your business from the ever-looming threats of the Dark Web.
Eager to explore further insights into safeguarding your business against data breaches? Ready to engage with us? Contact Us now and protect your business from future threats.

