Top Web Application VAPT Services in India | Invesics
Secure your web applications with comprehensive Web Application VAPT services from Invesics.
In 2023, cyber-attacks are expected to occur every 11 seconds. Don't let your web applications be vulnerable to such attacks.
Invesics offers comprehensive Web Application VAPT services to identify and fix potential security issues. With Invesics, you can skip the hassle of the traditional agency hunting process, proposal submission, consulting, and to-and-fro negotiations. Contact Us Now!

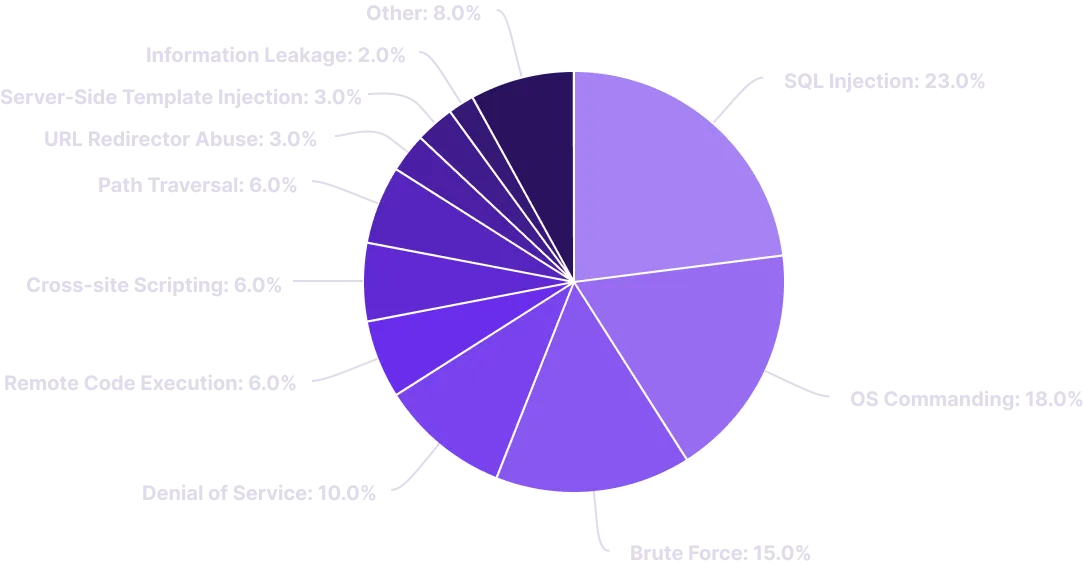

Our Research
What is Web Application Pen Test and why choose Invesics?
Web Application Pen Test is a proactive security testing method that identifies vulnerabilities and security holes that cybercriminals can exploit. Web applications are critical to business success, and it's essential to secure them against cyber threats.
At INVESICS, we offer a certified Web App Pen Testing team that includes Certified Penetration Professionals. Our team is highly trained and experienced in performing Web Application Security Testing and Website Security Testing to help your organization identify and remediate a wide range of risks.
Our Web App Pen Testing services provide you with the assurance that your web applications and corporate websites are secure, protecting your sensitive user and financial information against data breaches and reputational damage.
Choose INVESICS for reliable, top-notch Web Application Pen Testing services that help keep your web applications and corporate websites secure against cyber threats. Contact us today to learn how we can help you protect your business.
We Believe In Transparent Pricing
Powering your business with world class Web Application Pen Testing.
Our Scope
Website Application VAPT Scope
- Web Internet Gateway and Firewall Analysis
- Web Server Vulnerability Analysis
- Patch level testing and resulting vulnerabilities
- Cryptography related (layer 6)
- Misc Web Services called by Apps, XML Payloads
- Cloud login scenario testing
- Rootkit attack possibility and dormant ness
- SQL Injection and session stealing attack
- App code related (XSS, Cookie and many more)
- Backend Database reachability and Pentesting
- All are listed as BlackBox
- All are listed as GreyBox
- Scanning for 1000+ known code-level vulnerabilities
Web Application Common Attack Vectors
In cybersecurity, an attack vector is a method of achieving unauthorized network access to launch a cyber attack on a web application. The most common attack vectors include:
- Compromised Credentials
- Weak and Stolen Credentials
- Ransomware
- Missing or Poor Encryption
- Misconfiguration
- Brute force attack
- Distributed Denial of Service (DDoS)
- Zero-Day Vulnerabilities
Top 10 Web Application Vulnerabilities by OWASP
Our testing method includes assessing applications for vulnerabilities listed in the OWASP Top 10 but is not limited to. Our Web Application Security Testing team will help to identify and eradicate vulnerabilities including:
- A1 Injection
- A2 Broken Authentication
- A3 Sensitive Data Exposure
- A4 XML External Entities (XXE)
- A5 Broken Access Control
- A6 Security Misconfiguration
- A7 Cross-Site Scripting (XSS)
- A8 Insecure Deserialization
- A9 Using Components with Known Vulnerabilities
- A10 Insufficient Logging & Monitoring
Expert Cyber Security Solutions, at Tailor-made costing
That fit every requirement
Our Process
Web Application VAPT Process & Approach
Invesics's Pen-test approach goes beyond OWASP Top-10
Project Purpose
Requirement Gathering
Defining Scope
Automated VAPT
Manual PEN Testing
Review Analysis
Reporting Suggestions
Retest Certification
Experts strategy
In Web App VAPT our Security Experts perform the following steps:
When it comes to Web Application Vulnerability Assessment and Penetration Testing (VAPT), INVESICS security experts follow a comprehensive process to identify and remediate vulnerabilities in your web applications. Our Web App VAPT includes the following steps:
-
- Perform broad scans to identify potential areas of exposure and services
- Perform targeted scans and manual checks and investigations to validate vulnerabilities
- Test components to gain access
- Identify and validate the vulnerabilities
- Rank vulnerabilities based on threat levels, potential loss, and the likelihood of exploitation
- Identify issues of immediate consequence and recommend solutions
- Transfer knowledge to your organization on how to remediate and prevent future vulnerabilities
Choose INVESICS for reliable and top-notch Web Application VAPT services that help secure your web applications against potential areas of exposure and services. Contact us today to learn how we can help you protect your business.

Experience in below Domains but not limited to:


Our Deliverables
Our Web Application VAPT Deliverables
At INVESICS, we provide comprehensive Web Application Vulnerability Assessment and Penetration Testing (VAPT) services that include a range of deliverables to help you identify and remediate vulnerabilities in your web applications. Our Web Application VAPT deliverables include:
-
- Password-protected rich reporting for all scope
- Vulnerability listings with severity ratings to prioritize fixes
- Vulnerability listings are categorized by who needs to fix them (Developer, Server Admin, Network Admin)
- Evidence (Images or video) for each vulnerability to provide clear proof
- Conceptual fixings guidance for each vulnerability to suggest actionable solutions
- Explanation call with Dev/Fixing Team if required to clarify any doubts
- Complementary Re-Test within one month of Initial Report Submission to verify fixes and ensure your web applications are secure
Any Query?
Frequently Asked Questions
If it is tool based testing only, we will need URL in case of Web Application, APK file in case of Android App, IPA file in case of iOS App. If it is a manual based testing, along with previously mentioned things, we will need dummy credentials of each users roles exists in your system.
Yes, Invesics is an ISO 27001 certified Company. Resources who will work on the assignments are CEH certified. Security Lead at Invesics is a double graduate having Masters degree in Cyber Security and Incident Response.
INVESICS is ISO 27001 certified company and hence we have all the compliance applies to handle your data privacy. Further, you will get digitally signed NDA before starting the assignment, this NDA is legally valid.
You can convey that to you account manager, he will be there 24*7 to assist you. If your extra requirements does not fall under your selected plan, you will be given estimate for the extra work.
You can cancel the project anytime before signing NDA and you will get your money back. For more clarity, you can refer our refund policy here.
Relevant services
Supportive Cyber Security Services
Mobile Application Pen-Testing
Network Pen-Testing
Cloud Pen-Testing
Server Hardening
Under Attack? Need Immediate Assistance?
Reach out to our expert teammates to get solution for your Cyber Security concerns. We help to protect your organization from Data-breaches.