Guide to Android Application Hacking
In recent times, the significance of ethical hacking for Android apps and devices has grown exponentially. While traditional hacking is illegal, ethical hacking stands on the legal side. In illegal hacking, attackers or unauthorized individuals breach computer systems’ security to gain access to sensitive data. On the other hand, ethical hacking for Android involves deliberately hacking devices to uncover potential vulnerabilities and loopholes. Unlike illegal hacking, ethical hacking focuses on identifying weaknesses and bolstering security measures.
The surge in Android app usage has led to an increased demand for ethical hacking applications, resulting in a rising need for ethical hackers skilled in Android devices. As a result, more individuals are enrolling in Android hacking courses. These courses provide essential knowledge and ethical hacking skills to effectively become ethical Android hackers. This guide offers comprehensive insights into everything related to ethical hacking for Android apps and devices.
Why Opt for Ethical Hacking for Android Apps and Devices?
In today’s digital landscape, mobile phones, computers, and tablets have become indispensable in everyone’s daily life. As mentioned earlier, Android has emerged as one of the world’s most prevalent mobile operating systems, making millions of Android users susceptible to cyber-attacks and data theft. The vulnerabilities present in Android phones can lead to the compromise of critical data and information. To safeguard against such risks, ethical hacking for Android apps and devices has become an urgent necessity.
Choosing the best Android hacking course offers a deep understanding of the Android operating system’s architecture and ecosystem. It equips you with the knowledge of different Android components that often serve as gateways for malicious attacks. By enrolling in an Android ethical hacking course, you can enhance your expertise in Android attacks, thus significantly improving overall security. Additionally, opting for the Android ethical hacking course free allows you to expand your knowledge and skills without financial constraints.
Strengthening Application Security with Reverse Engineering
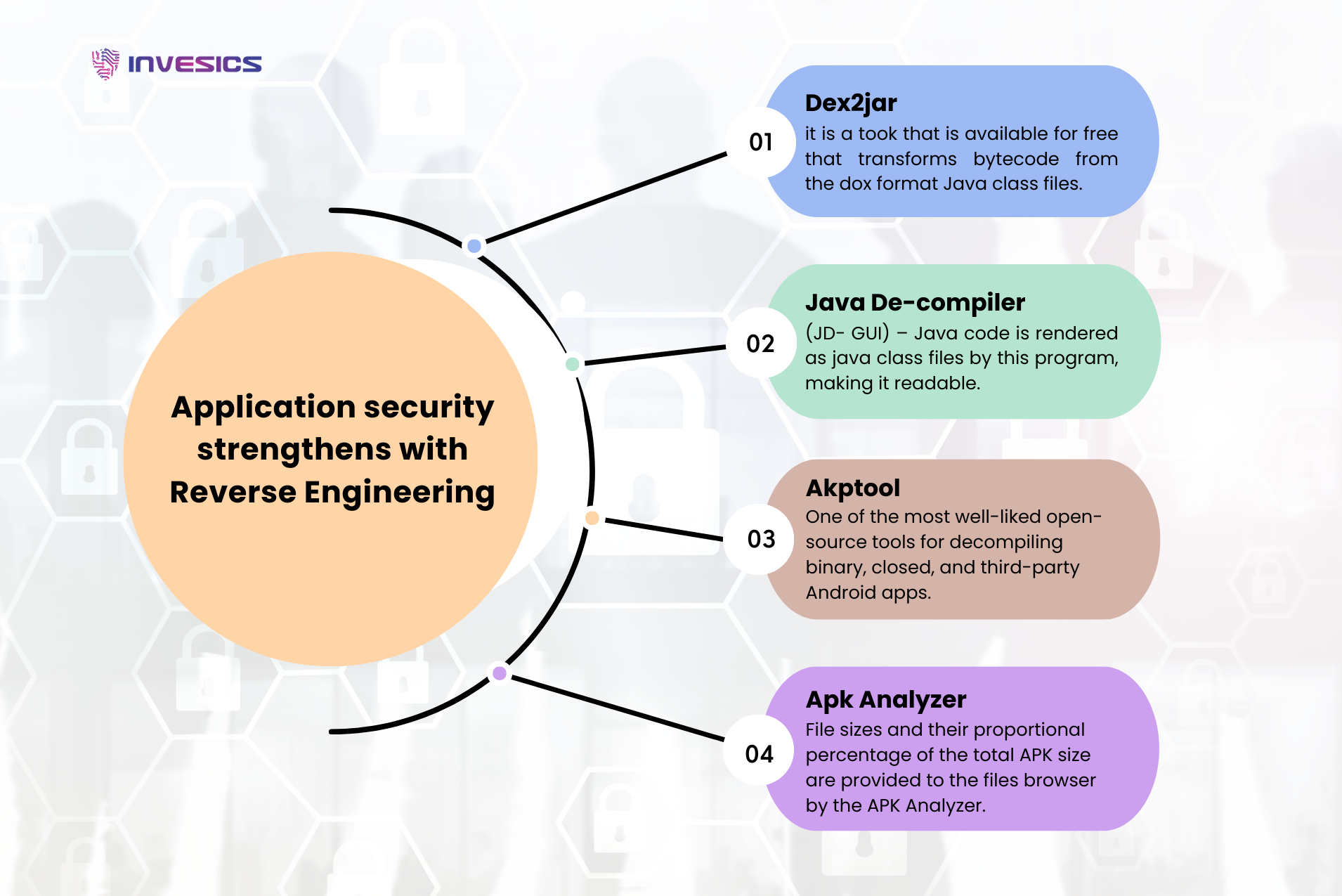
This blog delves into the intricacies of OWASP’s TOP 10 Mobile Vulnerabilities, Application Security using Reverse Engineering, and Android Application PenTesting. Ensuring high data security when dealing with Android applications is of utmost importance, making it a top priority. Reverse engineering is a powerful practice that extracts knowledge to enhance product development. To achieve this, we utilize various frameworks and tools:
- Dex2jar: A free tool that converts bytecode from the .dex format into Java class files, enabling analysis and improvements.
- Java De-compiler (JD-GUI): This program renders Java code as readable class files, facilitating understanding and modification.
- Akptool: Among the most popular open-source tools for decompiling binary, closed, and third-party Android apps, aiding in in-depth analysis.
- Apk Analyzer: Providing file sizes and proportional percentages of the total APK size, this tool assists in browsing and assessing APK components.
As Android apps are extensively used for mobile, banking, shopping, and sharing personal information, they become potential targets for cyberattacks using tactics like malware, code injection, and reverse engineering. Android Application Pentesting, also known as penetration testing, is the process of simulating a hacker’s approach to identifying security vulnerabilities in your own or your client’s IT systems.

Benefits of Android Application Pentesting:
- Enhanced Application Effectiveness: By uncovering vulnerabilities and weaknesses, pentesting helps make the Android application more robust and secure.
- Reduced Cost of Data Breaches: Identifying and addressing security flaws in advance decreases the risk and potential cost of data breaches.
- Client Trust and Confidence: Demonstrating proactive measures through pentesting builds clients’ trust and confidence in the application’s security.
- Comprehensive Security Assessment: Android Application Pentesting enables the discovery of potential security vulnerabilities, ensuring a comprehensive security evaluation.
In conclusion, utilizing reverse engineering practices and implementing Android Application Pentesting is crucial for strengthening application security. By understanding and addressing vulnerabilities, we can fortify Android apps against cyber threats, ensuring a safer and more resilient digital environment.
OWASP TOP 10 Mobile Vulnerabilities
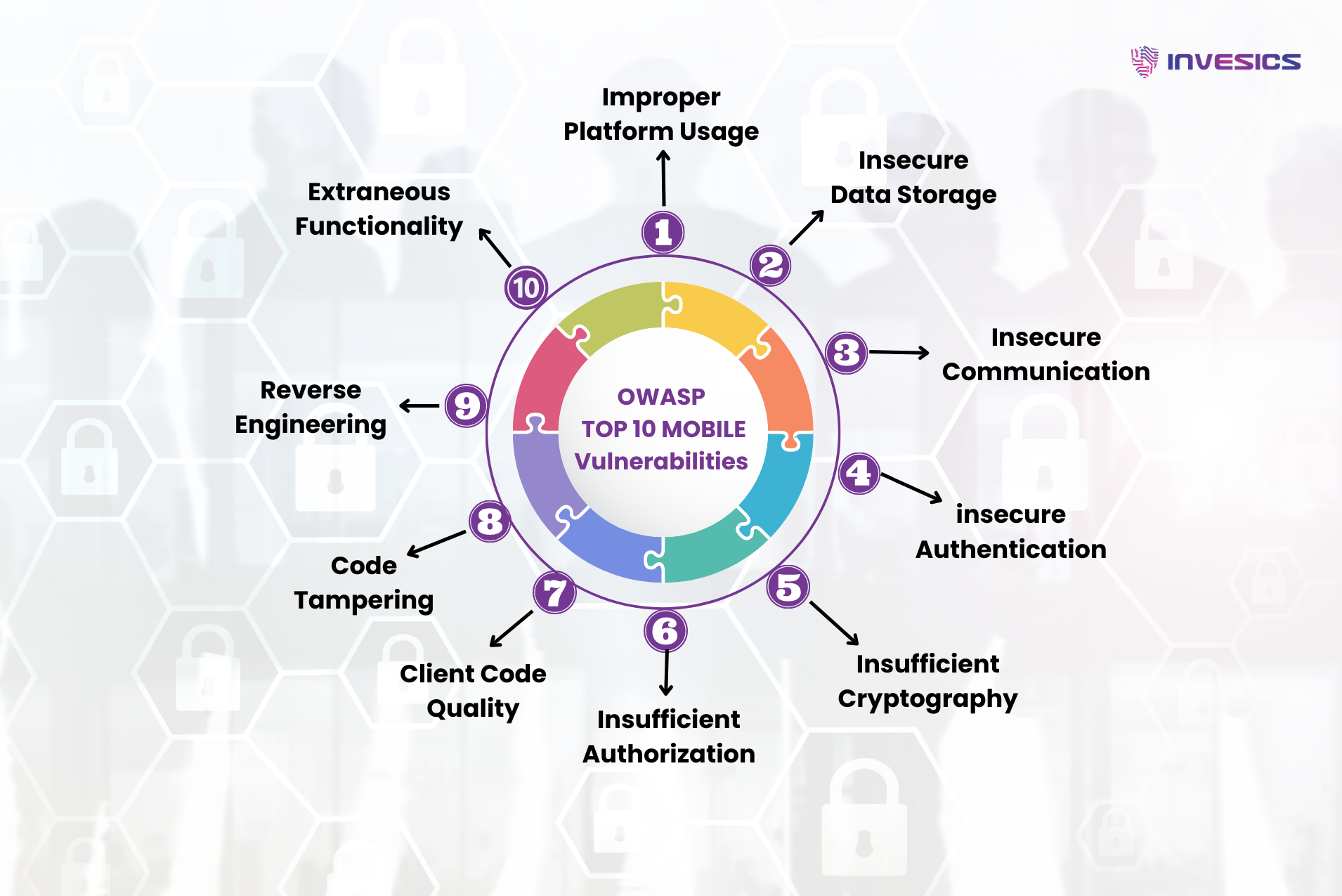
In the realm of software development, both web applications and security barriers present several risks. OWASP’s top 10 list of mobile vulnerabilities comprises common security issues that users may encounter. Here, we provide a concise overview of the top 10 security threats, ranked by the level of risk they pose. For further insights, refer to the details below:

-
Insecure Data Storage:
Data security is crucial for Android applications, as data is stored on servers, mobile devices, and cloud storage, making them vulnerable to hacker attacks. To avoid such risks, consider the following preventive measures:
- Prevent critical data from being stored on iOS devices.
- Implement an encryption layer.
- Avoid using hard-coded encryption or decryption keys.
-
Insecure Authentication:
Weak authentication can allow attackers to perform unauthorized actions through the app or backend server. Common examples include authentication bypass, information leakage via debug messages, and session invalidation. To address this, implement the following preventive measures:
- Implement two-factor authorization.
- Ensure authentication requests are performed server-side.
- Use an encrypted database.
- Avoid using spoofable values.
-
Insufficient Authorization:
The authorization ensures that only authorized individuals access data. Faulty permission implementation in mobile applications may grant low-level users access to high-privileged user information. Preventive measures include:
- Avoid relying on information from mobile devices.
- Verify roles and permissions of authenticated backend users.
-
Code Tampering:
Code tampering involves altering an application’s source code with harmful payloads, leading to business disruption and potential financial and reputational loss. To prevent code tampering, implement these preventive measures:
- Ensure the application reacts appropriately to code integrity violations.
- Detect execution within a jailbroken or rooted environment.
- Implement code change detection mechanisms.
-
Extraneous Functionality:
Attackers aim to comprehend hidden capabilities in the backend framework. Avoid including information about back-end tests or staging environments, as some auxiliary features may aid attackers. To prevent risks related to extraneous functionality, take the following steps:
- Verify all endpoints of the API.
- Check for hidden switches in the app’s configuration settings.
- Conduct manual code reviews with Subject Matter Experts (SMEs).
-
Improper Platform Usage:
This risk arises from the improper implementation or misuse of security controls in operating systems like iOS, Android, or Windows. Hazards in this category include breaking accepted norms, accidental abuse of functionality, and app best practices being overlooked. To prevent such risks, follow these measures:
- Avoid attempting to obtain access control through client applications.
- Do not place trust in the client.
- Thoroughly consider controls on the server side.
-
Insecure Communication:
Insecure communication channels may expose sensitive information to unauthorized individuals. The vulnerability of insufficient transport layer protection arises when developers fail to defend against network traffic threats. For prevention, consider these actions:
- Apply an additional layer of encryption.
- Avoid sending sensitive data.
- Use industry-standard cipher suites.
-
Insufficient Cryptography:
Weak encryption and decryption techniques may result in insufficient cryptography, allowing attackers to access private information. To enhance data security, take the following steps:
- Utilize modern algorithms recognized by experts.
- Use white box cryptography for high-security requirements.
- Utilize the application’s native chain.
-
Client Code Quality:
Poor code quality contributes to security incidents and data breaches. Buffer overflows and format string flaws are examples of dangers arising from poor code quality. To maintain code quality, consider these measures:
- Write well-documented code.
- Establish coding patterns agreed upon by the team.
- Validate incoming data to avoid buffer overflows.
-
Reverse Engineering:
Reverse engineering involves disassembling a mobile application to understand its logic, which can lead to unauthorized access or intellectual property loss. To mitigate reverse engineering risks, consider these measures:
- Implement code obfuscation to withstand deobfuscation.
- Obfuscate string tables and methods segments.
Prerequisites for Learning Android Ethical Hacking
Learning Android ethical hacking doesn’t require any prior knowledge, making it accessible to everyone. Whether you choose a comprehensive master’s program or an advanced Android hacking course, there are no specific prerequisites. All you need is a genuine interest in learning and growing in the field. However, having a basic understanding of the Android operating system and some familiarity with its usage will be advantageous. A fundamental grasp of information technology can also prove beneficial for individuals taking up the course.
Android Hacking Resources
As you dive into the realm of ethical hacking with Android, becoming familiar with Android hacking resources becomes essential. In cyber security certification courses, you’ll encounter numerous resources to enhance your Android hacking skills. Here are some of the best resources to explore:
- Android-Exploits: An open-source guide offering insights into various Android hacks and tools, including links to additional resources for Android ethical hacking.
- Veracode Community: Engage with security hackers, developers, and experts in the Veracode community to gain valuable insights into Android app development, modifications, and security.
- XDA Developers Forum: Join the extensive Android hacking and development community with millions of users for a wealth of knowledge and exchange of ideas.
- Hacking Android: 80 Pages of Expert’s Tutorials: A valuable resource for tutorials and codes on Android security, providing insights from monthly cybersecurity and hacking magazines.
By exploring these resources and honing your skills, you can embark on a rewarding journey into the world of Android ethical hacking. With determination and continuous learning, you can master the art of ethical hacking and contribute to the ever-evolving realm of cybersecurity.
The Top Three Threats to Android Devices
Threat One: Data in Transit
Mobile devices, including those operating on Android, are vulnerable to man-in-the-middle attacks and various exploits that target unsecured communications over public Wi-Fi networks and other wireless systems. By intercepting a user’s signal, attackers can impersonate legitimate web services, steal data, and intercept calls and text messages.
Threat Two: Untrustworthy App Stores
Unreliable app stores can lead to security issues due to their lack of robust security protocols. To ensure safety, opt for an Android app store that implements stringent security measures and follows a thorough security review program. Additionally, be cautious with sideloading, the process of installing apps from outside the official store, as it lacks foundational security measures.
Threat Three: SMS Trojans
Malicious apps may include SMS trojans, which exploit compromised applications. These trojans gain access to a mobile device’s calling or text messaging capabilities, allowing them to send harmful links to everyone in the user’s address book. Attackers can then distribute malware and malicious messages to fee-based services, causing financial harm to users and benefiting scammers.
Three Strategies to Safeguard Your Android Devices
-
Use TLS Encryption
Combat insufficient encryption by employing Transport Layer Security (TLS) to encrypt all internet traffic and securely generate and exchange session keys. TLS protection safeguards data against most man-in-the-middle and network spying attacks.
-
Test Third-Party App Security
Minimize the risk of malicious apps by exclusively downloading from the official Google Play store. Google Play enforces more stringent security checks compared to third-party sites, where hundreds of thousands of malicious apps may exist. If you must download from a third-party store, scrutinize app permissions before installation and be cautious of apps that request access to sensitive data or messaging without legitimate reasons.
-
Exercise Caution with SMS Payments
Ensure your Android phone limits apps’ ability to spend your money automatically. Be cautious of apps that request payment via SMS, as they may raise red flags. Avoid such apps whenever possible to protect yourself from potential financial risks.
By implementing these security measures, Android users can significantly reduce the risk of falling victim to the top threats and maintain a safer mobile experience.
Enhance Your Organization’s Android Penetration Testing with INVESICS:
Conducting thorough vulnerability assessments for Android apps is an essential yet complex process in mobile application development. Ensuring the security of sensitive data is paramount for the proper functioning of these apps.
To scrutinize your apps comprehensively and uncover hidden errors and weaknesses, developers need expertise in reverse engineering. Our OWASP MSTG CrackMe tasks are designed to help you cultivate the fundamental skills necessary for this crucial task.
At INVESICS, we boast adept teams comprising Android developers, testers, reverse engineers, and QA professionals who excel in making your mobile apps reliable and secure. Our human and automated VAPT services adeptly identify, detect, and analyze vulnerabilities in your IT infrastructure, elevating your awareness of potential risks. Furthermore, we offer security auditing for compliance, ensuring your company adheres to established rules and legislation by various governments.
Reach out to us to have your Android app thoroughly tested and fortified for enhanced security. Let INVESICS assist you in fortifying your app’s defenses and ensuring your users’ data remains safeguarded.


